Table of Contents
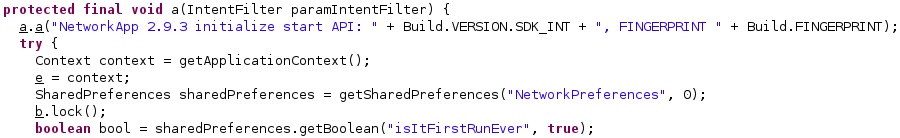
Pegasus is a spyware developed by the NSO group that was repeatedly analyzed by Amnesty International and CitizenLab. In this article, we dissect the Android version that was initially analyzed by Lookout in this paper, and we recommend reading it along with this post. During our research about Pegasus for Android, we’ve found out that vendors wrongly attributed some undocumented APK files to Pegasus, as highlighted by a researcher here. We’ve splitted the analysis into 3 parts because of the code’s complexity and length. We’ve also tried to keep the sections name proposed by Lookout whenever it was possible so that anybody could follow the two approaches more easily. In this last part, we’re presenting the WAP Push messages that could be used to autoload content on the phone without user interaction, the C2 communication over the MQTT protocol, the exploitation of a vulnerability in MediaPlayer that was not disclosed before, and the ability of the spyware to track phone’s locations.