Table of Contents
Over 1,600 publicly available Docker Hub images hide malicious behavior, including cryptocurrency miners, embedded secrets that can be used as backdoors, DNS hijackers, and website redirectors.
Docker Hub is a cloud-based container library allowing people to freely search and download Docker images or upload their creations to the public library or personal repositories.
Docker images are templates for the quick and easy creation of containers that contain ready-to-use code and applications. Therefore, those looking to set up new instances often turn to Docker Hub to quickly find an easily deployable application.
Unfortunately, due to abuse of the service by threat actors, over a thousand malicious uploads introduce severe risks to unsuspecting users deploying malware-laden images on locally hosted or cloud-based containers.
Many malicious images use names that disguise them as popular and trustworthy projects, so threat actors clearly uploaded them to trick users into downloading them.
Researchers at Sysdig looked into the issue, trying to evaluate the scale of the problem, and reported on the found images that feature some form of malicious code or mechanism.
Docker Hub traps
Apart from images reviewed by the Docker Library Project, which are verified to be trustworthy, hundreds of thousands of images with an unknown status are on the service.
Sysdig used its automated scanners to scrutinize 250,000 unverified Linux images and identified 1,652 of them as malicious.
The largest category was that of crypto-miners, found in 608 container images, targeting server resources to mine cryptocurrency for the threat actors.
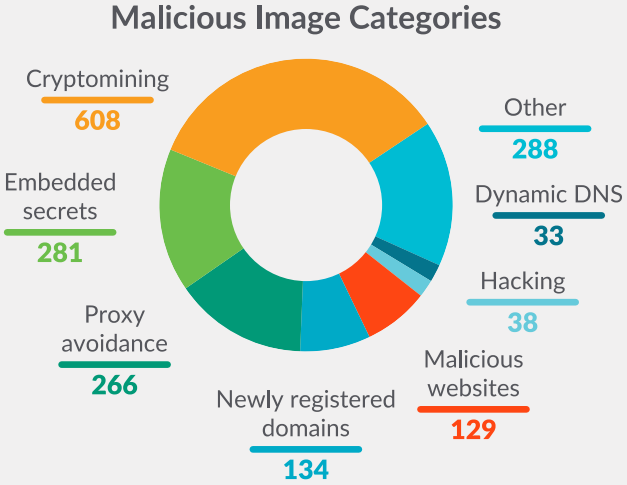
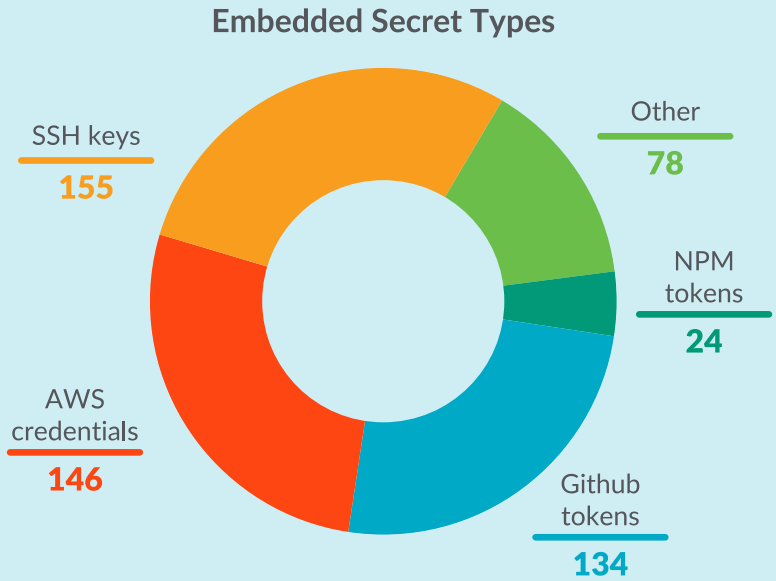
The second most-common occurrence were images hiding embedded secrets, measuring 281 cases. The secrets embedded in these images are SSH keys, AWS credentials, GitHub tokens, NPM tokens, and others.

#SupplyChain







