Table of Contents
On Telegram, Killnet hackers have leaked a text file showing the login credentials of 10,000 individuals whom they claim are FBI agents.
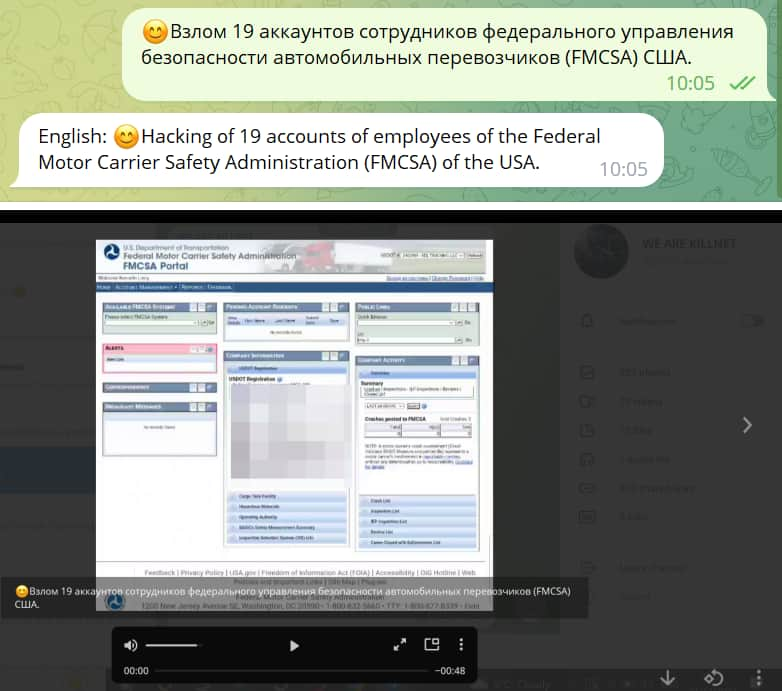
The hacker group also claimed to have breached the security of the US Federal Motor Carrier Safety Administration (FMCSA).
The Russian hacker group, KillNet, claims to have infiltrated the FBI’s database, allegedly stealing the personal information of more than 10,000 US federal agents. Like most of their attacks, this alleged attack also appears to have political undertones motivating the pro-Kremlin group.
It is worth mentioning that, just last week, the FBI’s security platform InfraGard suffered a data breach in which the personal data of its 87,000 members was stolen and leaked online.
Although Killnet’s attack remains unverified, KillNet hackers claim that the stolen data includes social media passwords and bank details. The group posted screenshots on Telegram that showed passwords to online stores, medical ID cards, and Google, Apple, and Instagram accounts.
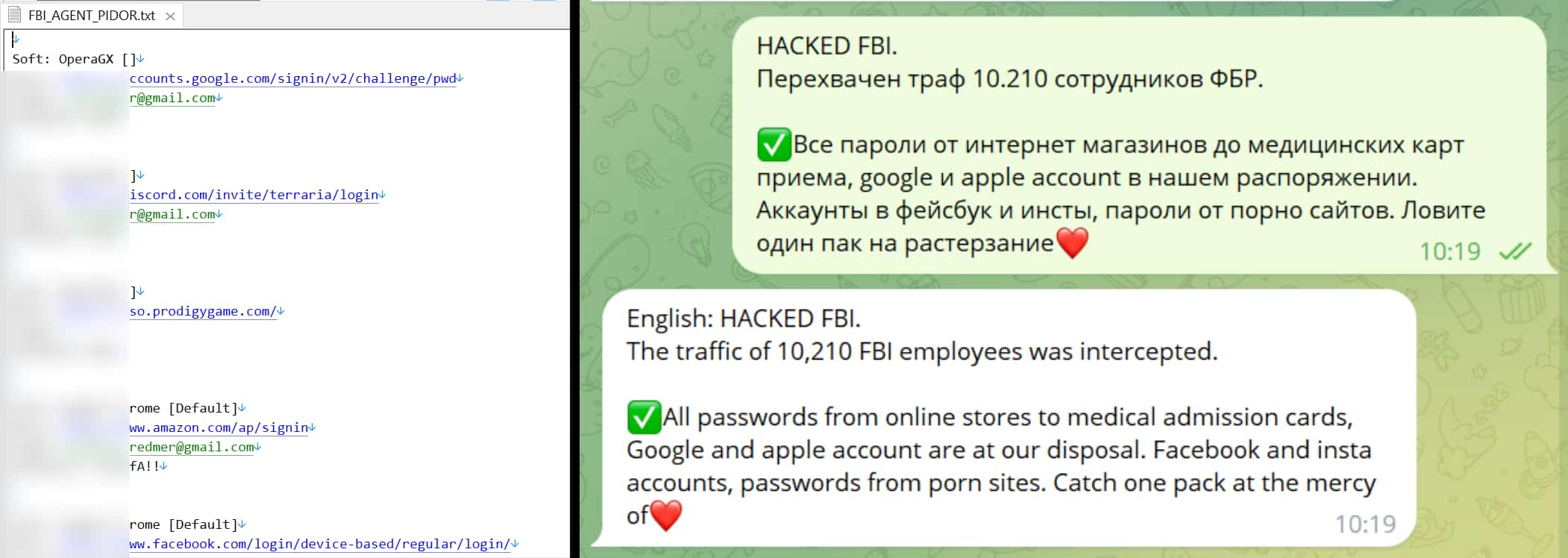
“All passwords from online stores to the mass acceptance card, Google, and Apple accounts are at our disposal,” read a statement attributed to the hackers on Russian Telegram channels.
As seen by Hackread.com, another screen recording showed the hackers using the Facebook account allegedly belonging to an employee of the Federal Motor Carrier Safety Administration (FMCSA). They show being in control of the account by posting “We are KillNet” on the person’s profile page.