Table of Contents
Threat Actors Exploiting Silicon Valley Bank (SVB) Collapse Scenario To Launch Cyber-Attacks
Following a bank run on its deposits, Silicon Valley Bank (SVB) experienced a failure on March 10, 2023, and has garnered significant media attention. As SVB has traditionally been the preferred banking partner for many startups worldwide, its failure is expected to significantly impact this community.
The collapse of SVB has been severe, with many startups now facing financial instability and even potential layoffs. As a result, these affected companies seek alternative funding means to keep their businesses running. However, this search for financial stability has made them a prime target for Threat Actors (TAs) who are taking advantage of the current situation by conducting various malicious activities.
Cyble Research & Intelligence Labs (CRIL) has identified several suspicious websites that have emerged in the wake of the SVB collapse.
Suspicious domains are below:
- svbcollapse[.]com
- svbclaim[.]com
- svbdebt[.]com
- svbclaims[.]net
- login-svb[.]com
- svbbailout[.]com
- svb-usdc[.]com
- svb-usdc[.]net
- svbi[.]io
- banksvb[.]com
- svbank[.]com
- svblogin[.]com
Some websites emerged after March 10, 2023, right after the collapse of SVB, and have raised concerns about potential threats. These sites appear to have been developed by TAs who are looking to exploit the current situation for their personal gain.
On March 13, 2023, the Department of the Treasury, Federal Reserve, and FDIC issued a joint statement to safeguard all depositors’ funds and ensure access to their money. However, despite being a relief for affected depositors, Threat Actors have started using this announcement to launch their malicious campaigns. The following cryptocurrency scam is a typical instance of this trend.
Crypto fraud exploiting SVB Collapse Crisis
While monitoring phishing activity, CRIL has detected several crypto phishing schemes that are taking advantage of the current situation surrounding the collapse of SVB to deceive unsuspecting victims. These phishing sites, namely svb-usdc[.]com and svb-usdc[.]net, have set up a bogus USDC reward program claiming that “Silicon Valley Bank is actively distributing USDC as part of the SVB USDC payback program to eligible USDC holders.” They aim to steal cryptocurrency from the victim’s account by offering them free USDC.
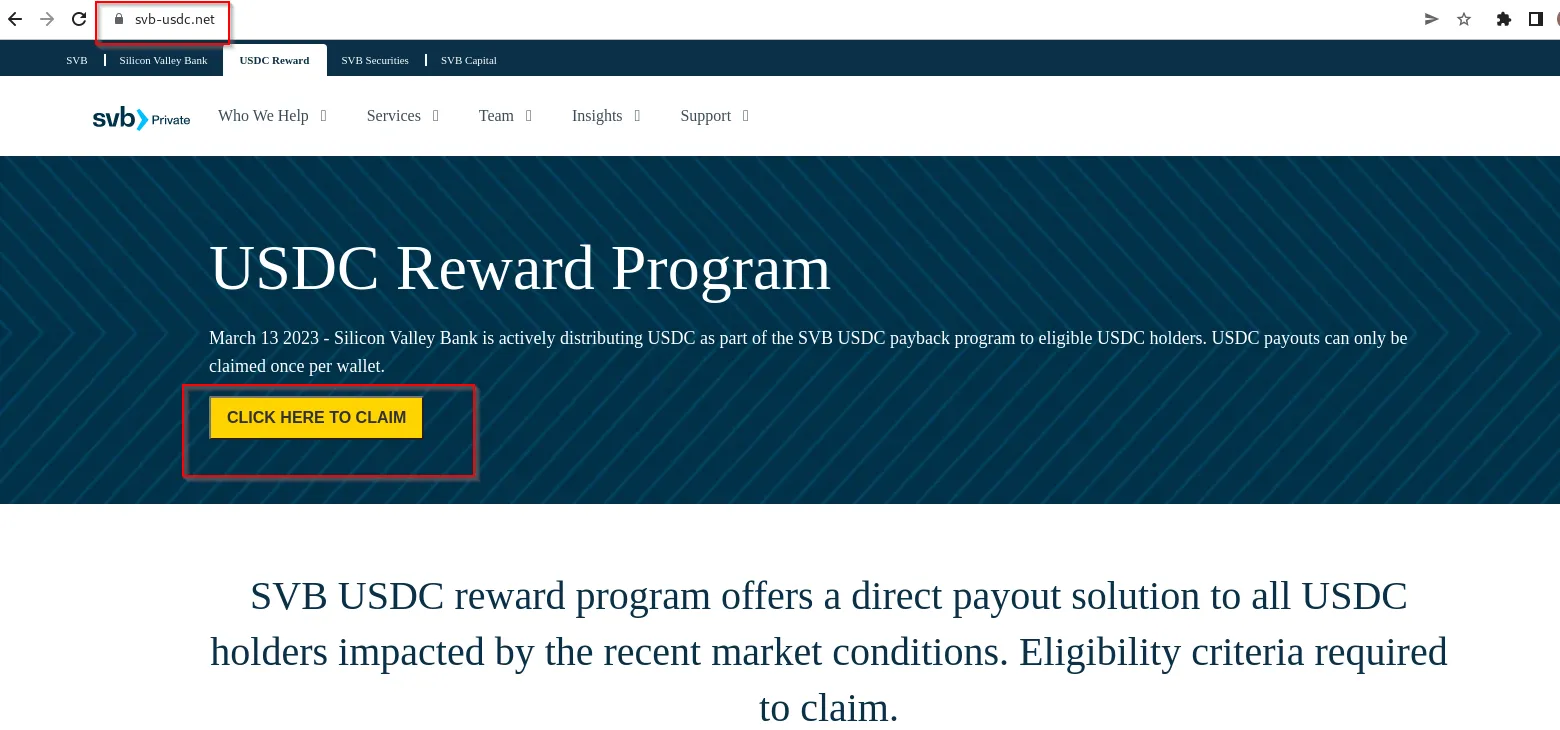
A QR code will be displayed if a user clicks on the “CLICK HERE TO CLAIM” button to receive the promised USDC on the phishing site. The victim is instructed to scan this QR code using any cryptocurrency wallet, such as Trust, Metamask, or Exodus. However, scanning the code will result in the compromise of the user’s wallet account.
Likewise, on March 13, 2023, Circle, the issuer of USD coins, announced that they held $3.3 billion worth of USDC with SVB and would resume their operations.
Additionally, Circle stated that USDC would remain redeemable 1 for 1 with the U.S. Dollar. Shortly after this announcement, CRIL noticed several phishing sites pretending to be Circle and promoting a deal of 1 USDC for 1 U.S. Dollar.
Below is the list of phishing websites using the same crypto scam trend:
- hxxps://redeemed-circle[.]com
- hxxps://circle-reserves[.]com
- hxxps://circleusdcoin[.]com
- hxxps://circle-mintusdc[.]com
- hxxps://svb-circle[.]com
- hxxps://circle.web3claimer[.]net
- hxxps://usd-circle[.]com
Furthermore, CRIL discovered that several unidentified funding firms have approached affected organizations, offering funds during the SVB collapse.
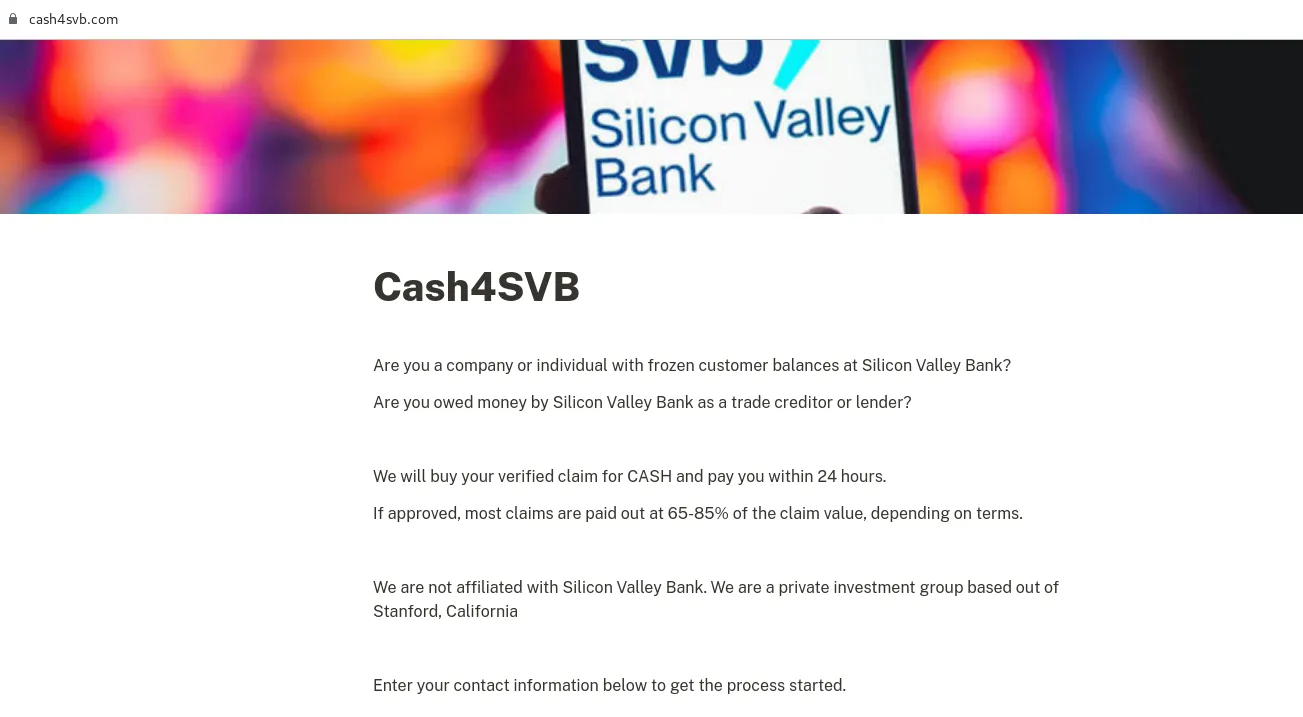
On the day of SVB’s collapse, March 10, 2023, a questionable website with the URL hxxps[://]cash4svb[.]com was created. This website, allegedly created by an anonymous investment group, offered cash to affected organizations, as illustrated in the figure below.
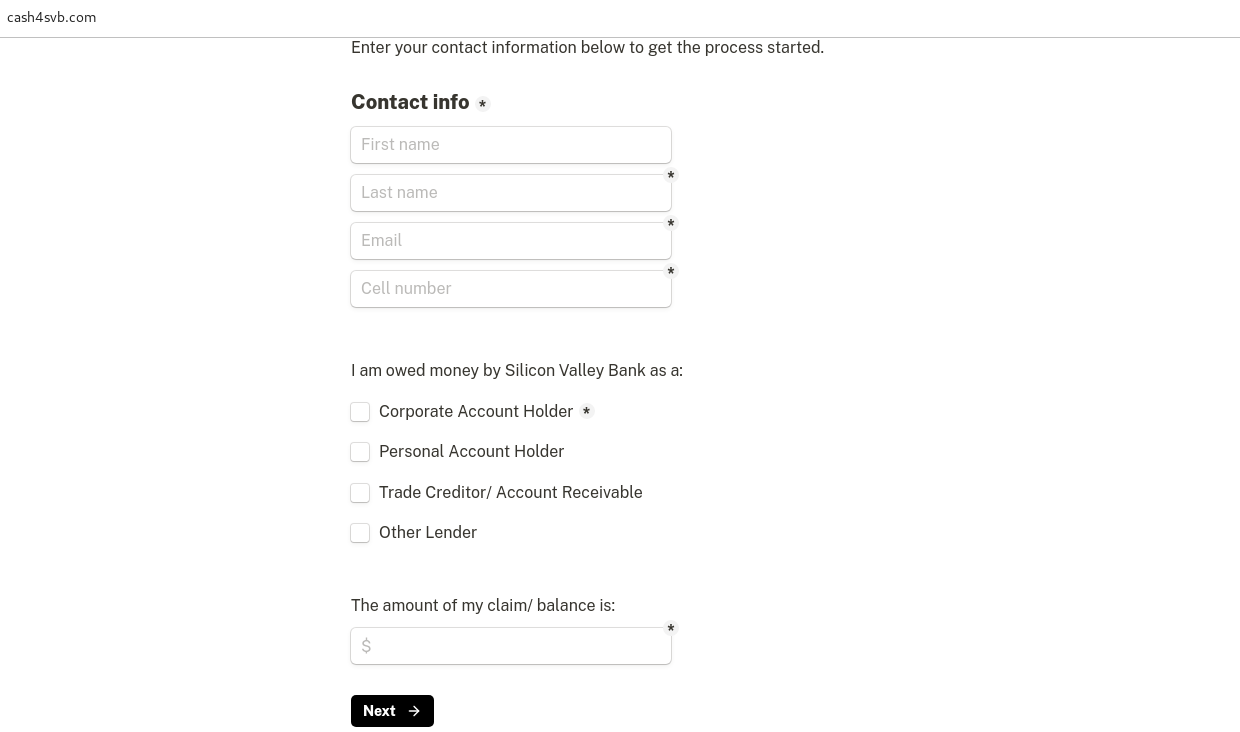
The site requested users to provide personal information such as their name, email, mobile number, and balance amount to process a claim, as shown in the figure below.
It is suspected that these anonymous investment groups gather contact information through certain websites during an SVB collapse and may potentially sell the information of affected organizations to third-party funding companies. Additionally, they may offer loans to struggling companies at exorbitant interest rates, among other activities.
Conclusion
TAs often take advantage of ongoing scenarios and events to launch mass infection campaigns, and users may fall for these scams due to fear, a sense of false urgency, and a lack of attention.
Given the recent buzz surrounding the collapse of SVB, which will have long-lasting effects on affected organizations, these entities are likely to become targets for TAs who may employ malware and phishing attacks to victimize them.
The phishing websites identified by CRIL appear to have been designed to target organizations impacted by the SVB collapse and steal cryptocurrency using masqueraded phishing sites. Therefore, affected organizations must remain alert and take proactive measures to safeguard their sensitive data from potential cyber threats.
Recommendations
- Avoid downloading files from unknown websites.
- Use a reputed anti-virus and internet security software package on your connected devices, including PC, laptop, and mobile.
- Refrain from opening untrusted links and email attachments without first verifying their authenticity.
- Educate employees on protecting themselves from threats like phishing/untrusted URLs.
- Monitor the beacon on the network level to block data exfiltration by malware or TAs.
- Enable Data Loss Prevention (DLP) Solutions on the employees’ systems.

#Finance #Cryptocurrency #IoCs








