Table of Contents
Western countries don't appear to have an answer or robust knowledge about the operators behind Ghostwriter (aka UNC1151), a threat actor that has been engaged in a mixture of hack-and-leak and dis/misinformation campaigns over the past half-decade, a report [PDF] from Cardiff University has concluded.
The group, believed to contain a mixture of Belarussian and Russian operators, has been active since 2016. Its activities have included hacking news sites to post fabricated stories, planting manufactured documents on government websites, and leaking doctored evidence across social media.
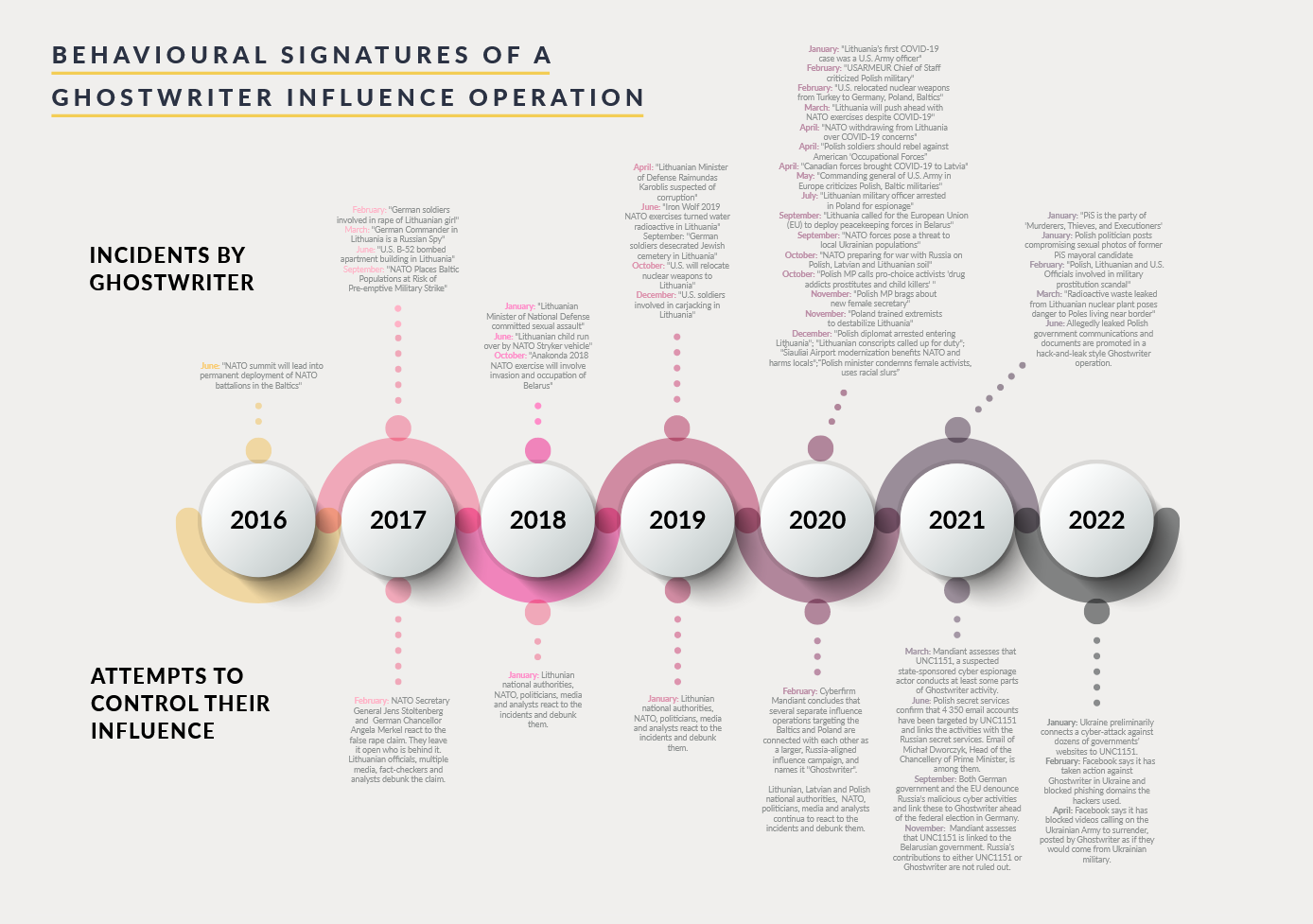
Unlike the IRA and Russia's other internet troll farms and influence operations, Ghostwriter works on a higher level. Operations are timed and planned to coincide before or during important political events or military exercises, often requiring public rebuttals and clarifications from the targeted governments or politicians.
Researchers say because the group mixes both cyber (hacking) and psyop (influence) components, the group has gone under the radar for many years and has yet to be fully understood. Their theory blames the West's confusion about who's supposed to investigate GhostWriter. Is it a country's cybersecurity or its intelligence agency? Is it the private infosec community, or is Ghostwriter official government spook business?
As the researchers point out, this confusion and lack of understanding of the level where GhostWriter operates had allowed the group to run around for four years between 2016 and 2020 before people caught on to what they were doing and that the group existed.
The Cardiff University team believes Western countries are completely unprepared to deal with a group of GhostWriter's level. They lack "robust knowledge of the specific operators behind it," and they are accustomed to using a playbook for dealing with influence operations that was designed to go after low-level social media meme spam from the Internet Research Agency.
"The EU has not put its cyber sanctions toolbox into use and designated sanctions on those responsible for Ghostwriter's activity. [...] No countries, at least based on public knowledge, have used offensive cyber capabilities to target Ghostwriter's activities. Likewise, none of the social media platforms have public reporting on Ghostwriter's activities on their platforms equal to that provided for the IRA, where the public pressure for accountability led the companies to change their policies."
The research team's main proposals focus on more collaboration and intelligence sharing, both between the countries typically targeted by the group and government and private sector players.
It's these cracks that GhostWriter has exploited in the past, knowing that getting a coordinated response from multiple governments, social media networks, and private companies has always been difficult—time during which Ghostwriter was able to cultivate and spread their dis/misinformation.
Just like law enforcement and cybersecurity firms have gotten together to go after, disrupt, and dox ransomware operators, the same level of success can be achieved against Ghostwriter once a more coordinated and centralized effort is put into countering its operations.
"Ghostwriter's partial successes in evolving and expanding its activity is likely due to a mix of limitations in attribution; intelligence sharing; varying level of understanding; requiring responses to the threat in different countries to involve different political actors, as well as social media platforms."









