Table of Contents
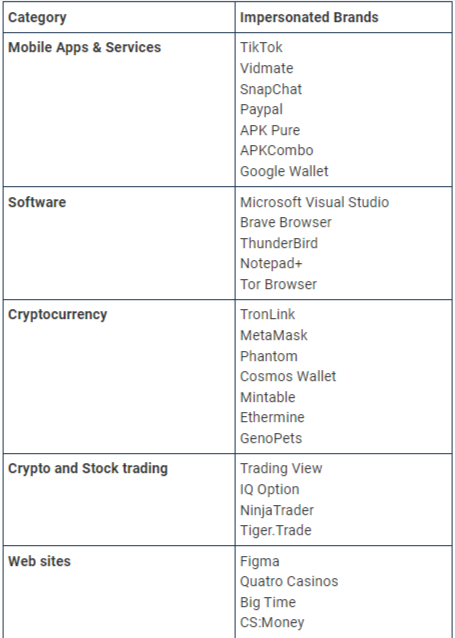
A massive, malicious campaign is underway using over 200 typosquatting domains that impersonate twenty-seven brands to trick visitors into downloading various Windows and Android malware.
Some of the malicious sites were discovered by cyber-intelligence firm Cyble, which published a report this week focusing on domains mimicking popular Android app stores like Google Play, APKCombo, and APKPure, as well as download portals for PayPal, VidMate, Snapchat, and TikTok.
While Cyble's report focused on the campaign's Android malware, BleepingComputer found a much larger typosquatting campaign from the same operators, distributing Windows malware.
This campaign consists of over 90 websites created to impersonate over twenty-seven popular brands to distribute Windows malware, steal cryptocurrency recovery keys, and, as described above, push Android malware.